Whistleblower Aid play a critical role in upholding transparency and accountability within organizations and governments. By exposing corruption, fraud, and other malpractices, whistleblowers contribute significantly to the public interest. However, the act of whistleblowing is fraught with risk, often exposing individuals to retaliation and legal consequences. To mitigate these risks and provide a secure avenue for reporting, platforms like Whistleblower Aid have emerged.
Whistleblower Aid is a secure platform that operates on the dark web. Enabling whistleblowers to anonymously upload and report sensitive information. This platform is an integral part of the SecureDrop project, an initiative spearheaded by the Freedom of the Press Foundation. The primary objective of Whistleblower Aid and SecureDrop is to ensure the safety and anonymity of sources. Thereby encouraging more individuals to come forward with critical information without fear of retribution.
Their mission is to expose corruption, safeguard press freedoms, and protect journalists and their sources. By hosting Whistleblower Aid, the foundation provides a robust infrastructure that leverages advanced encryption technologies to secure the identities of whistleblowers.
In essence, Whistleblower Aid and SecureDrop serve as essential tools in the fight for transparency and accountability. They empower individuals to report wrongdoing safely and anonymously, thereby fostering a culture of integrity and openness. As more people become aware of these resources, the potential for uncovering and addressing systemic issues grows, ultimately benefiting society as a whole.
Accessing Whistleblower Aid: Tools and Steps Required
To ensure maximum security and anonymity when accessing Whistleblower Aid. It is crucial to utilize specific tools and follow certain procedural steps. One of the primary tools required is the Tor Browser. Which allows users to access dark web sites safely and securely. Downloading the Tor Browser is straightforward: visit the official Tor Project website and select the appropriate version for your operating system. Once downloaded, follow the installation instructions carefully. Upon installation, open the browser and configure it according to the provided guidelines. Which typically involve adjusting privacy and security settings to their highest levels.
In addition to the Tor Browser, incorporating a VPN further enhances security by masking your IP address and encrypting your internet connection. For the highest level of anonymity, it is advisable to purchase a VPN service using Bitcoin. Choose a reputable VPN provider known for its strong security features and no-log policy. To purchase the VPN with Bitcoin, first set up a Bitcoin wallet and buy Bitcoin from a trusted exchange. Next, visit the VPN provider’s website, select a subscription plan, and choose Bitcoin as the payment method. Follow the on-screen instructions to complete the transaction.
Once you have acquired the VPN service, download and install the VPN software on your device. Open the VPN application and connect to a server, preferably one located in a privacy-friendly jurisdiction. After establishing the VPN connection, launch the Tor Browser to add an additional layer of security. This combined approach ensures that your online activities remain anonymous and secure. Significantly reducing the risk of exposure when accessing Whistleblower Aid.
By meticulously following these steps and utilizing the recommended tools, individuals can confidently navigate Whistleblower Aid. Ensuring their actions remain confidential and their identities protected.
Navigating Whistleblower Aid: Setting Up and Using Your Codename
After successfully accessing Whistleblower Aid through the Tor Browser and a VPN, the next critical step is setting up your codename. This codename functions as both your username and password, playing a paramount role in maintaining your anonymity and security.
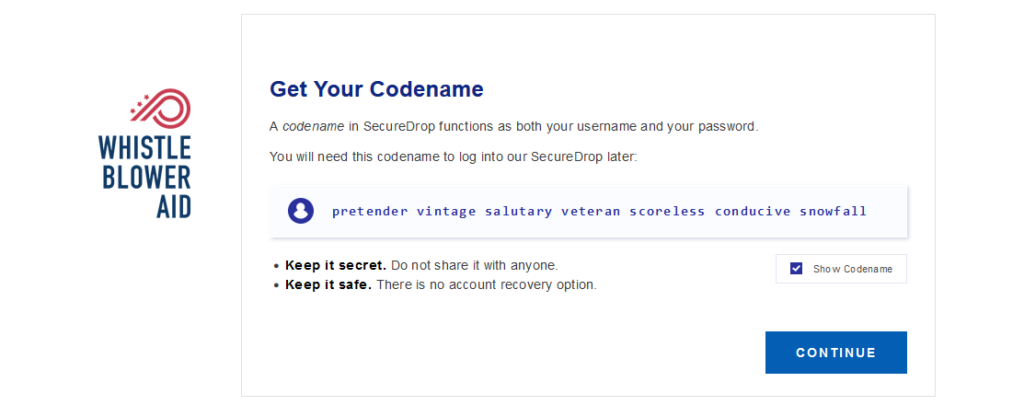
To generate a robust codename, you should ideally combine a mix of uppercase and lowercase letters, numbers, and special characters. Avoid using easily guessable information such as birthdays, common words, or sequences. A strong codename minimizes the risk of unauthorized access and fortifies your security within the Whistleblower Aid platform.
Once you have created a suitable codename, it is crucial to store it securely.
Open the Tor Browser, navigate to Whistleblower Aid, and enter your codename when prompted. Ensure your VPN is active throughout this process to preserve your anonymity. Always log out from SecureDrop after completing your session to prevent unauthorized access.
Maintaining your security while using Whistleblower Aid involves several best practices. Avoid accessing the platform from public Wi-Fi networks or shared computers. Always use the Tor Browser and a VPN to mask your online activities. By adhering to these guidelines, you can maximize your security and maintain the confidentiality of your communications.
Best Practices for Secure Reporting and Uploading Information
Ensuring the security of the information you report through Whistleblower Aid is paramount. As you navigate this secure platform, it’s essential to adhere to best practices for securely uploading sensitive documents and communicating effectively. One of the primary steps in safeguarding your data is the removal of metadata from files. Metadata can include hidden details such as the creation date, author information, and file history, which could inadvertently reveal your identity.
Another critical aspect is the use of encryption tools to protect your data. Encrypting your documents ensures that even if intercepted, the information remains inaccessible without the correct decryption key.
Understanding the platform’s security features is also vital. Familiarize yourself with these features to leverage them fully. Additionally, maintaining your anonymity involves avoiding digital footprints.
Moreover, ensure the confidentiality of your communications by using secure messaging apps that offer end-to-end encryption.





I am extremely impressed together with your writing skills and also with the layout for your weblog. Is that this a paid subject or did you customize it yourself? Either way stay up the excellent high quality writing, it is uncommon to see a great blog like this one these days