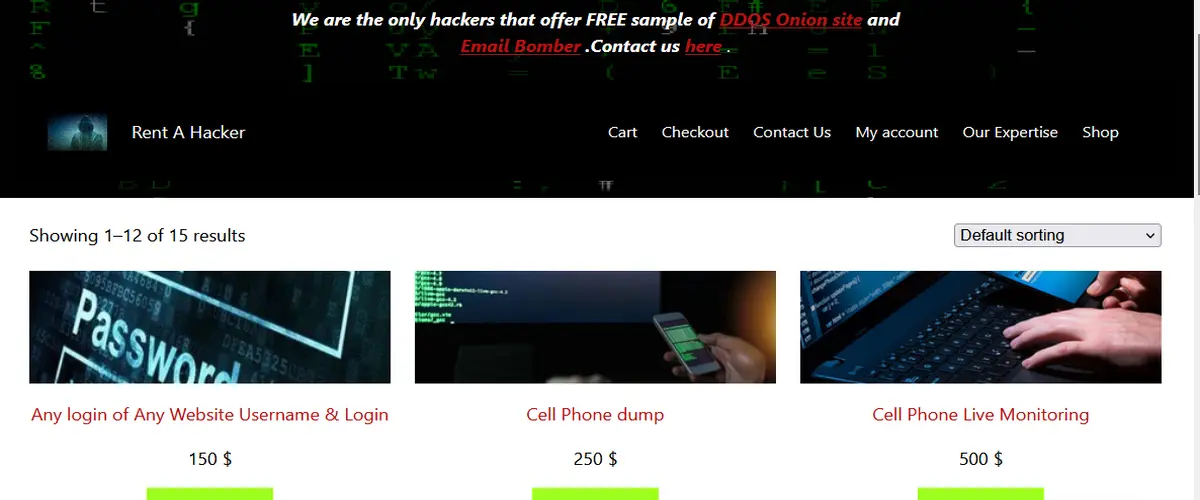
Rent a Hacker website is a notable entity on the dark web. Offering a range of hacking services to individuals seeking unauthorized access to digital information. Among the various services provided, phone surveillance stands out as a prominent feature. This service allows clients to monitor phone activities, intercept messages, and access call logs. Thereby gaining insight into the target’s private communications.
On this platform, clients can also request services such as email hacking, social media account breaches, and data retrieval from various devices. User ratings and reviews play a critical role in establishing the credibility of hackers available for hire. These reviews often highlight the successful completion of tasks and the professional conduct of the hackers. Which can significantly influence the decision-making process of prospective clients.

The dark web, a hidden part of the internet accessible only through specific browsers like Tor. Serves as a marketplace for various illicit activities, including hacking services. Individuals and organizations might turn to ‘Rent a Hacker’ for numerous reasons, including espionage, financial gain, or personal vendettas. The anonymity provided by the dark web ensures that both clients and hackers can operate with a reduced risk of detection by law enforcement.
As personal and professional lives become increasingly intertwined with technology. The information stored on digital devices becomes a valuable target for those with malicious intent. Consequently, the demand for hacking services, particularly phone surveillance, continues to grow. Driven by the need to access and control sensitive information.

Accessing ‘Rent a Hacker’ Website
Accessing the ‘Rent a Hacker’ website on the dark web necessitates stringent privacy measures due to the inherent risks involved. The first essential step is to use a privacy-focused browser equipped with Tor,. Which facilitates anonymous browsing by routing your internet traffic through multiple servers. This process ensures that your online activities remain concealed from prying eyes.
To begin, download the Tor Browser from the official Tor Project website. The software is available for various operating systems, including Windows, macOS, and Linux. After downloading, proceed with the installation by following the on-screen instructions. Once installed, open the Tor Browser and click on the ‘Connect’ button to initiate a secure connection to the Tor network.
For enhanced security, configure Tor Browser settings to maximize privacy. Navigate to the ‘Preferences’ or ‘Settings’ menu and adjust the security level to ‘Safest’. This action disables certain web features that may compromise your anonymity. Additionally, it is advisable to avoid installing browser plugins or extensions, as they can inadvertently leak identifying information.
Beyond the Tor Browser, consider using additional tools to bolster your security. A VPN can provide an extra layer of encryption, masking your IP address even before it reaches the Tor network.
While navigating the dark web, exercise caution by avoiding the use of personal information and refraining from downloading unknown files. The ‘Rent a Hacker’ website, like many dark web sites, operates in a legally ambiguous space. Therefore, maintaining a high level of security and privacy is paramount to protect yourself from potential legal and cyber threats.
Communicating with the Vendor
Secure communication is paramount when dealing with vendors on the dark web, particularly those offering hacking services. The anonymity and security measures in place help protect both the vendor and the client from potential legal repercussions and cyber threats.
To initiate communication with a dark web vendor. It is crucial first to register an email account on the dark web. Popular dark web email providers include ProtonMail, Tutanota, and Mail2Tor. These services offer end-to-end encryption, ensuring that the content of emails is accessible only to the sender and recipient. ProtonMail and Tutanota are accessible via both the surface web and the Tor network. While Mail2Tor is exclusively available through Tor. This exclusivity can provide an additional layer of security.
When registering for a dark web email account, it is essential to avoid using any personal information that could potentially identify you. Furthermore, consider utilizing a random password generator to create a strong, unique password. To enhance your security posture, avoid reusing passwords across multiple accounts.
A VPN masks your IP address and encrypts your internet traffic, providing an extra layer of security and anonymity. When selecting a VPN, prioritize those with a strict no-logs policy, strong encryption protocols, and a reputation for reliability. NordVPN, ExpressVPN, and CyberGhost are popular choices among privacy advocates.
Maintaining anonymity is critical when engaging with dark web vendors. Always access the dark web via the Tor browser. Utilize a secure and anonymous email service, and employ a reliable VPN. By adhering to these practices, you significantly mitigate the risks associated with dark web communications.
Payment Methods and Security
The ‘Rent a Hacker’ website on the dark web facilitates transactions primarily through cryptocurrencies. Including Bitcoin, Litecoin, Bitcoin Cash, and Dogecoin.
Bitcoin, the most widely recognized cryptocurrency, is often the go-to choice due to its vast acceptance and robust security measures. Similarly, Litecoin offers faster transaction times and lower fees, making it an attractive alternative. Bitcoin Cash, a fork of Bitcoin, provides larger block sizes, enabling quicker processing of transactions. Dogecoin, initially created as a joke, has gained popularity for its low transaction costs and rapid confirmation times.

Using cryptocurrencies for transactions on the dark web offers significant benefits. The primary advantage is anonymity. This decentralization ensures that users can conduct transactions without revealing their true identities. Providing a layer of privacy crucial for dark web activities.
Security is another vital benefit. Cryptocurrencies use blockchain technology, which records transactions on multiple nodes, making it nearly impossible to alter or counterfeit. This ensures that transactions are secure and verifiable, reducing the risk of fraud.
After setting up a wallet, users can purchase cryptocurrencies from exchanges using traditional currencies. The volatility of cryptocurrency values can lead to significant fluctuations, impacting the amount paid or received. Additionally, while transactions are anonymous, they are not completely untraceable. Law enforcement agencies have developed advanced techniques to trace cryptocurrency transactions back to users.
To mitigate these risks, users should employ additional security measures such as using anonymous browsing tools like Tor. Regularly updating their software to protect against vulnerabilities, and being cautious of phishing schemes. By taking these precautions, users can enhance their security while navigating the dark web.







Great Service . Only legit shop
Ordered the cell phone dump . Received it 24 houres . Verry skilled hackers
sceptical first but seller delivers
After getting scammed for someney times i finally found this legit site. They were able te recover my lost email password
I have ordered a few times here already and the seller always deliver what you ordered
Le vendeur est sympathique. J’ai commandé la “cell phone live monitoring”. C’est le seul vendeur sur le dark web qui fait ce qu’il dit .
Great hacker , great service
Hands down greatest hacker . Tnx for the Cell Phone Dump !
Only and best hacker the darknet
Just desire to say your article is as amazing. The clarity in your submit is just spectacular and that i can suppose you’re an expert in this subject. Well along with your permission let me to clutch your feed to keep up to date with drawing close post. Thanks one million and please carry on the gratifying work.
You can certainly see your skills in the work you write. The world hopes for even more passionate writers like you who aren’t afraid to say how they believe. Always follow your heart.
I’d incessantly want to be update on new articles on this internet site, bookmarked! .